Recent research conducted by the Cyber Security Research Institute (CSRI) demonstrates how easy and common it is for threat actors to purchase stolen digital certificates in order to bypass security solutions. In this blog, we will use this research to show how Intezer Analyze™ deals with signed malware files, even if it has a legitimate certificate.
Software publishers purchase costly certificates from a trusted certification authority in order to prove their integrity. Many security vendors tend to trust files containing valid digital signatures and automatically classify them as trusted, giving these files a green light to run on machines.
Easy access to stolen certificates means bypassing standard security protocols, which can be done quite easily, having a high implication on security measures.
Since Intezer Analyze™ differs from common threat detection methods by only looking at the code and searching for code reuse, this solution can’t be fooled by stolen certificates.
**List of malware containing legitimate certificate: http://signedmalware.org/
The well known Stuxnet worm found in 2010, believed to have caused substantial damage to Iran’s nuclear program, used two separate stolen certificates.
In addition to Stuxnet, CCleaner, a more recent attack, is another infamous example of malware using stolen certificates to bypass existing security protections. Hackers hid malware in CCleaner software distributing it to millions of users, exploiting the trust held between consumers and vendors.
The actual malware detected in CCleaner was found to contain malicious code: the attackers implanted their code in a legitimate product that received a legitimate certificate.
Interesting findings of the latest research shows the extent of the method:
“We identify 325 signed malware samples in our data set. Of these, 189 (58.2%) samples are properly signed while 136 carry malformed digital signatures, which do not match the binary’s digest. Such malformed signatures are useful for an adversary: we find that simply copying an Authenticode signature from a legitimate sample to an unsigned malware sample may help the malware bypass AV detection. The 189 samples signed correctly rely on 111 unique certificates. We find that only 27 certificates were revoked; malware signed with one of the remaining 84 certificates would still be trusted today as long as is carries a trusted timestamp. “ stated CSRI.
Intezer Analyze™ does not care about certificates. Our malware analysis service is providing an extensive understanding of any executable file by comparing code on a massive scale to a comprehensive database of malware and trusted software.
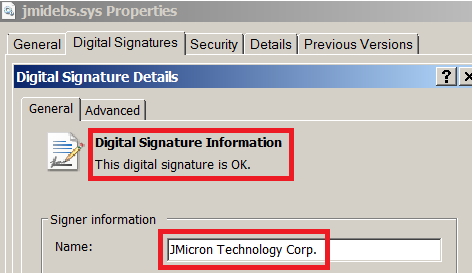
For instance, certain samples of Zeus, a very popular banking trojan, used stolen digital certificates. Although these samples are signed, Intezer Analyze™ was able to detect the malware immediately.
Here is the certificate of this file:
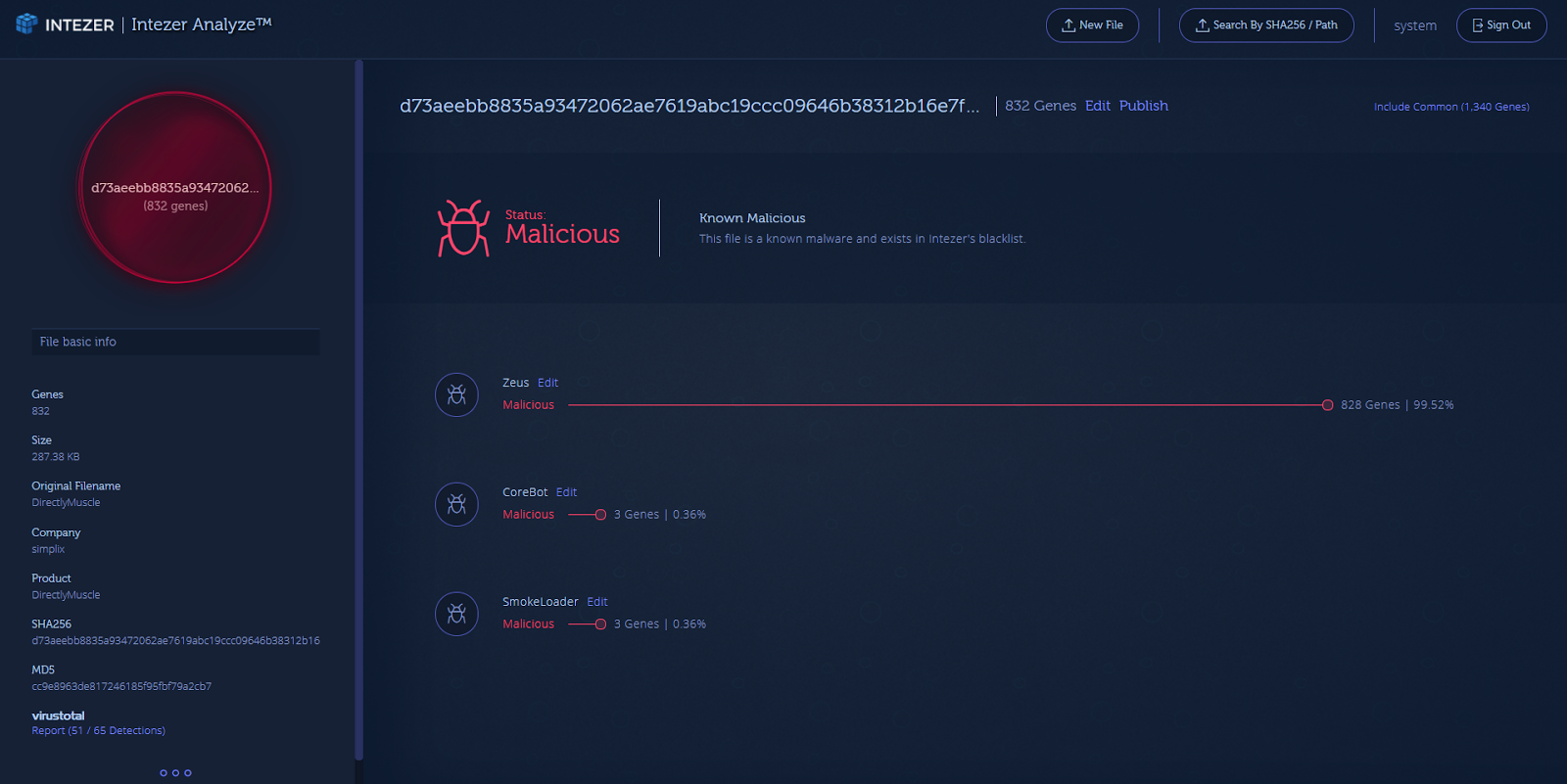
And this is the analysis report of the file at Intezer Analyze™:
https://analyze.intezer.com/#/analyses/4d77b764-384c-4fa6-a6d3-94bd2870d406
Although this malware sample was signed with a digital certificate, Intezer Analyze™ identified Zeus code and instantly classified it as malicious.
Intezer Analyze™ engine is powered by Code Intelligence technology performing ‘DNA Mapping’ for software. The engine enables the analysis and identification of the origins of every tiny piece of code, within seconds. This technology dissects any given file or binary into thousands of small fragments, and then compares them to Intezer’s Genome Database, which contains billions of code pieces from legitimate and malicious software offering an unparalleled level of understanding of any potential threat.
Once again we see that identifying the origins of files by finding code reuse is very valuable in the scenario of malware signed with digital certificates.
We invite you to read more in our blog and register to the free community edition of Intezer Analyze.