For mid to large size enterprises, protecting the organization against targeted cyber threats is often a global operation. It’s not uncommon for organizations to have several security operations centers (SOCs) disseminated globally in regions such as the Americas, APAC, and EMEA. While individual SOCs may be focused on protecting a specific region, these teams can benefit from one another by sharing information such as:
1) The classification of targeted threats
2) Effective remediation tactics on previous incidents
Intezer’s Malware Analysis technology enables security teams to automatically detect and classify cyber threats, based on identifying code reuse and similarities seen in previous threats. With Intezer Analyze’s private indexing feature, SOCs from the same organization can automatically share classifications and remediation tactics on unknown files, to reduce the time spent on investigating previously seen threats and quickly and effectively tailor their response.
Create your Own Genetic Database!
Intezer Analyze enterprise users can privately index malware and proprietary software in order to:
1) Quickly reduce false positives and duplicate alerts
2) Detect targeted threats
3) Accelerate incident response, across multiple SOC teams within the same organization
Advantages:
• Privately index your own, trusted software to quickly reduce false positives and duplicate alerts
• Privately index targeted threats to share classification and remediation tactics on previous incidents
• Label files for transparency among all SOC teams
• Accelerate response by prioritizing known threats with previously effective remediation
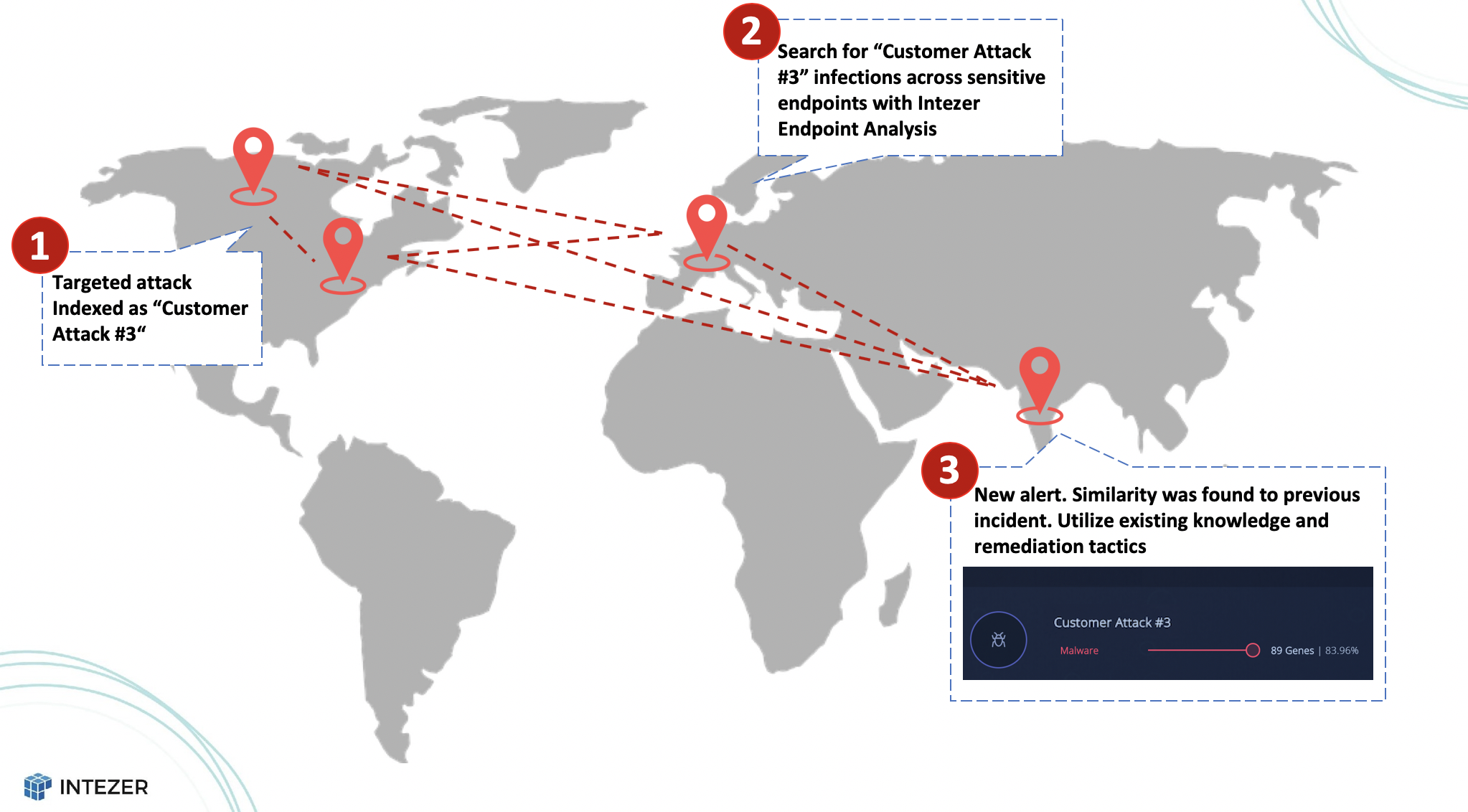
For example, if a SOC in the United States identifies a targeted attack using Intezer Analyze, they can classify and index the threat as “Customer Attack #3.” Any future threat that reuses even the smallest percentage of code will be automatically detected as “Customer Attack #3.” In other words, SOCs can quickly identify whether a particular threat is related to a previous incident, and can consult with their SOC teams from other regions for guidance on effective remediation tactics to quickly close the incident.
Once “Customer Attack #3” has been indexed, SOCs can scan for infections across their sensitive endpoints using Intezer’s endpoint analysis feature. In addition, security teams can quickly and easily export a code-based YARA signature in Intezer Analyze, to proactively hunt for variants of the threat that may be targeting their organization in other regions. Since Intezer’s YARA signatures are based on a threat’s malicious and unique code only—and not trusted code from shared or embedded libraries—the signatures will generate more accurate hits.
Intezer has a thorough and well-documented API that can fully automate the use cases mentioned above. For more information about Intezer’s private indexing feature, request a demo today: https://intezer.com//contact-us/.