AI and Next-Gen Automation for Your SOC
- Auto-resolve false positives and escalate only 4% of alerts for immediate response
- Deep, automated incident investigations with actionable response recommendations

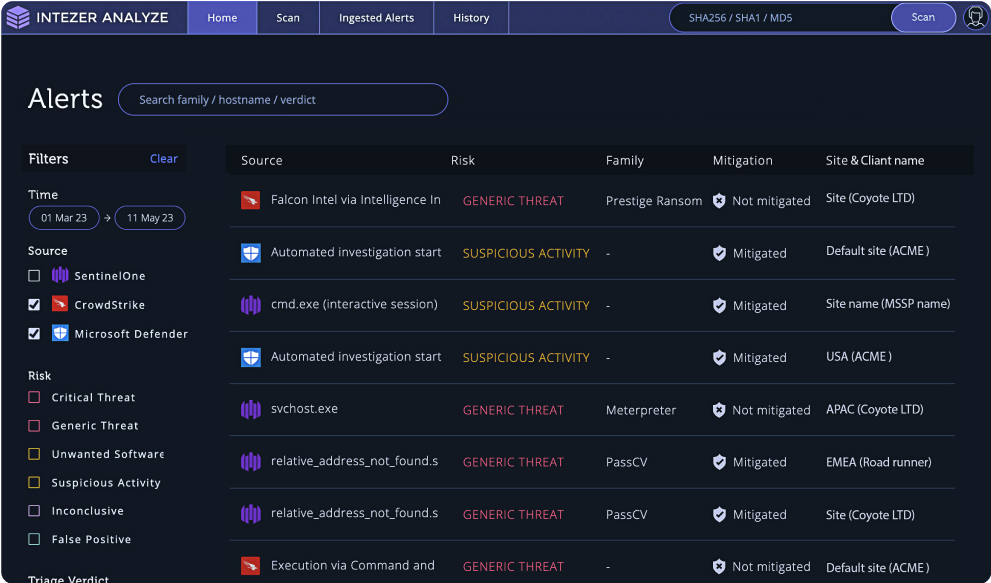
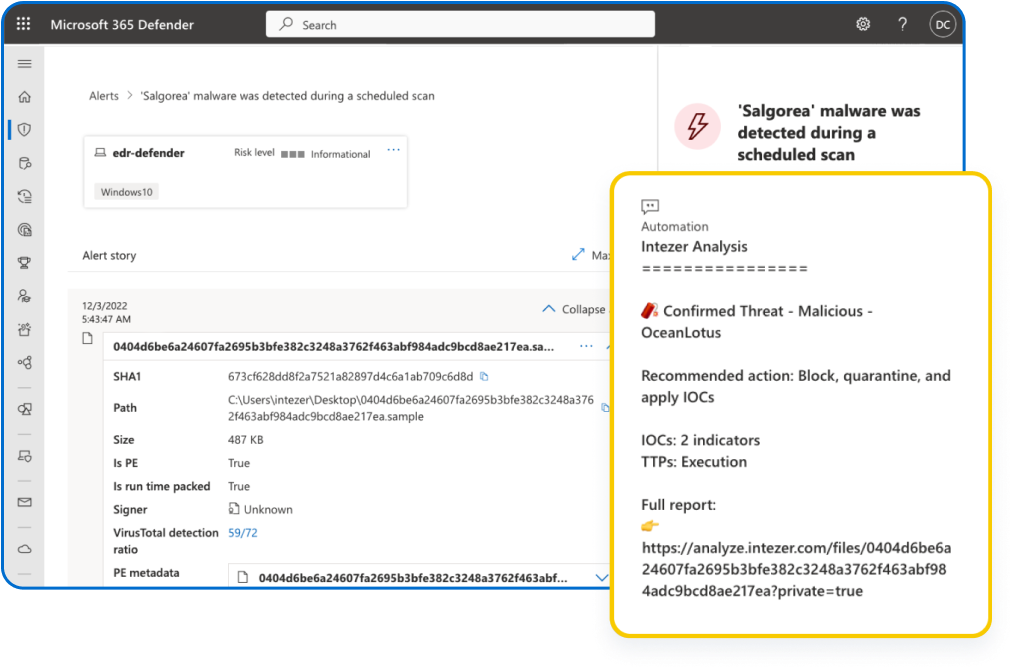
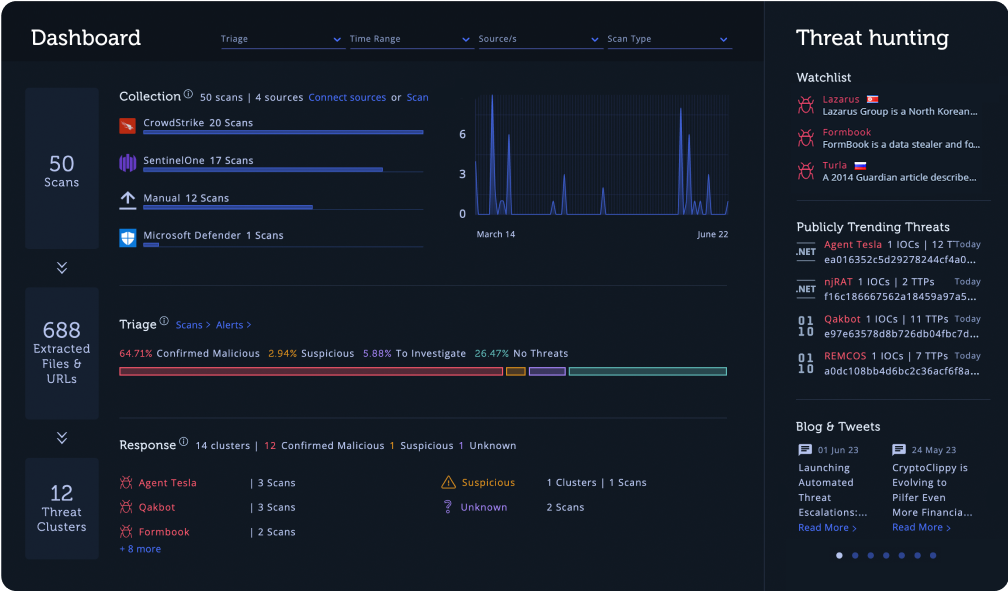
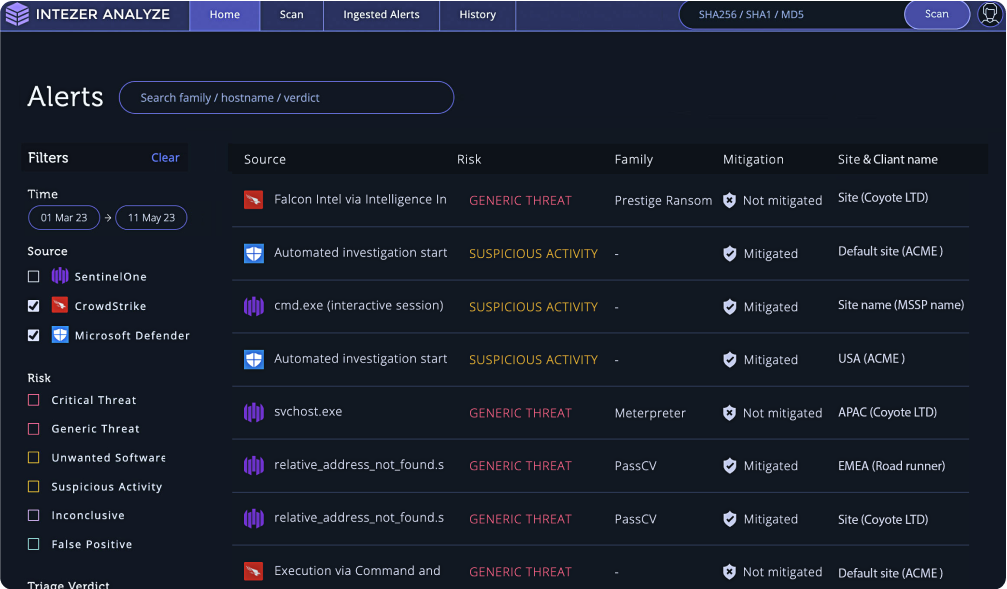
Intezer automatically ingests alerts from your connected sources 24/7 and collects evidence.
Intezer investigates evidence related to each alert to determine a clear classification, assessment, and recommended next steps.
Intezer auto-resolves false positives, escalating only the important incidents to your team with a complete analysis report.
Intezer auto-remediates confirmed threats and provides ready-to-use rules for response and hunting.
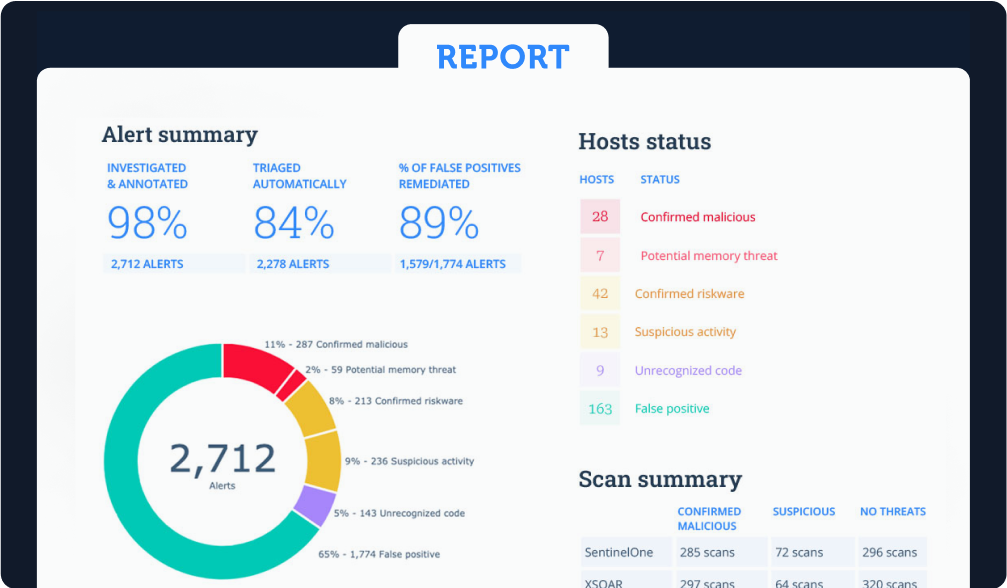
Intezer generates weekly reports to provide suggestions and give you full visibility over your security operations and alert pipelines.

Just minutes to set up, no engineering required. Within a minute after each new alert, get assessments and recommended actions pushed from Intezer right to your endpoint security console or SOAR.


















Connect Intezer to your security tools (endpoint, SIEM, SOAR, etc.) with an API key or plugin.

Intezer automatically ingests your alerts, analyzing all relevant artifacts (files, URLs, memory images) with artificial intelligence.
You get up to 97% of false positives auto-resolved, clear recommendations for every alert, and high-priority threats escalated.
Curious about Intezer and our technology? Check out our Frequently Asked Questions page to learn more.
Intezer leverages propriety artificial intelligence models, a variety of trusted techniques, and unique Genetic Code Analysis technology. For crafting the bottom-line incident triage assessments, Intezer uses machine learning and AI models that take into account the multiple analysis results for each individual evidence alongside information from the user’s existing security tools. You can read more in our blog post here about Intezer’s AI Framework.
Intezer’s automated alert triage process starts by collecting all evidence associated with an alert (file, process, command line, IP, URL, memory image, etc.), deeply analyzes each artifact, and then builds an overall assessment for the incident with smart recommendations. If you want to read more about the five stages in this autonomous process, you can check out our blog post about how the Autonomous SOC platform works.
Intezer can ingest and triage alerts from endpoint security products, SIEM tools, user-reported phishing pipelines, and SOARs. Intezer can also integrate with tools for ticketing and case management, such as ServiceNow.
Some of our most popular integrations are for CrowdStrike, SentinelOne and Microsoft Defender to automate endpoint security alert triage and response.
Intezer can also be interacted with and perform automated security operation tasks through our RESTful API and Python SDK.
Check out our full Integration list here.
Intezer’s AI-driven technology functions as an extension of your team to help you further reduce your SOC/IR workload, often working side-by-side with your existing security stack.
The primary onboarding tasks are connecting your alert sources and then adding members of your team as new users to your Intezer account.
It takes a few minutes to connect a security tool as a new alert source in Intezer, using an API key with the necessary permissions. After adding your API key to Intezer, you should start seeing alert triage results in your dashboard within the hour. If you want to know more about getting started with Intezer, you can book a demo to talk with us about integrating Intezer into your tech stack and team’s processes.
Top brands like Pepsico, Adobe, Equifax, Anheuser-Busch InBev, and other Fortune 500 enterprise security teams use Intezer to triage the high volume of alerts (and all the associated artifacts) from their endpoint and email security systems. Enterprise organizations also use Intezer’s Autonomous SecOps capabilities across their SOC.
To find out how other companies are using Intezer’s AI-powered platform, check out our case studies here.
If you want to try Intezer for yourself, you can sign up for a free Autonomous SOC account with a 2-week trial of the Complete plan. For an extended trial with support from our Solution Engineers, reach out to book a demo here.