Cryptocurrency is trending. Bitcoin traded at a record high nearly $42,000 this month. Now Ether, the world’s second largest cryptocurrency, is closing in on all-time high.
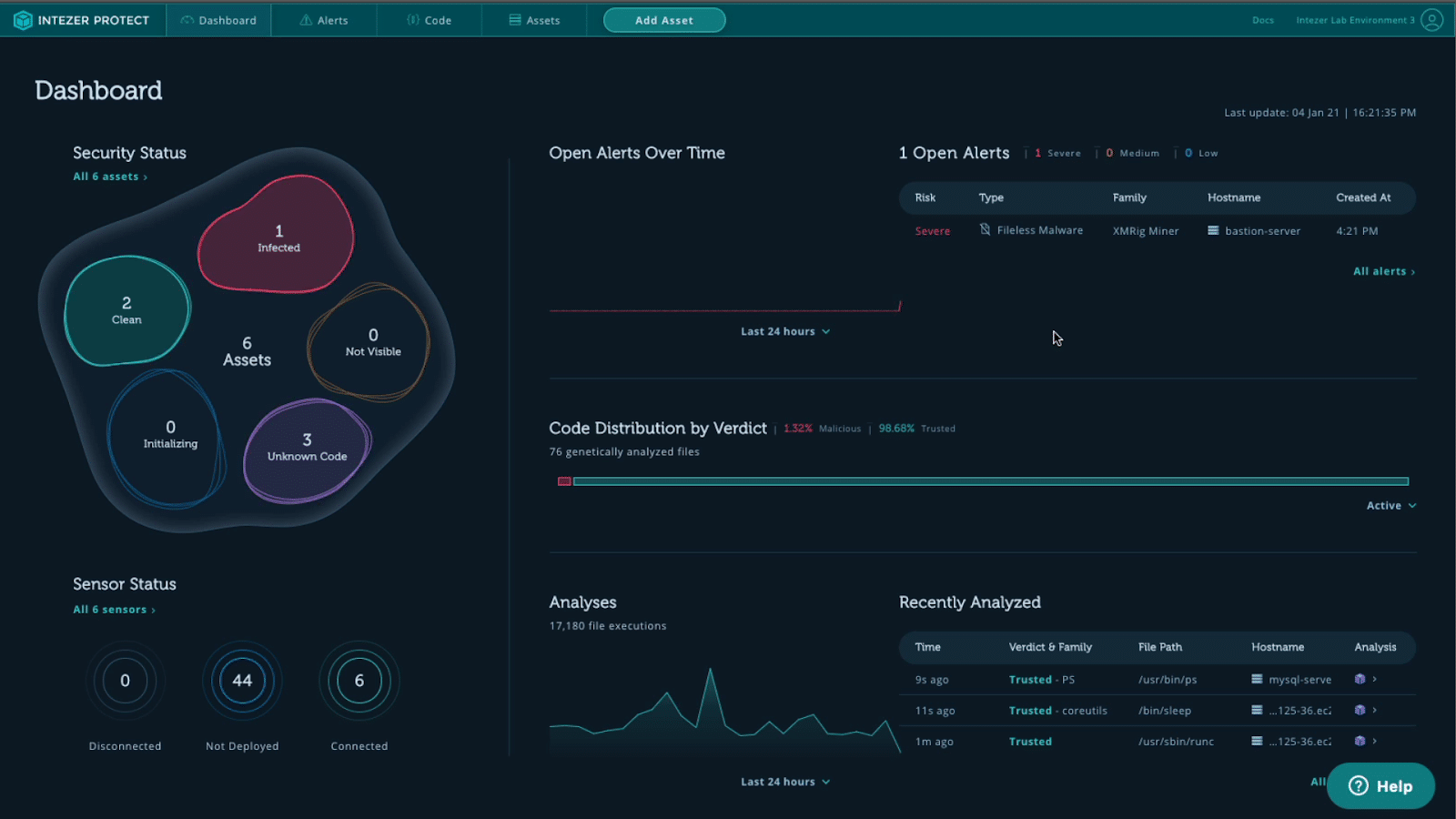
Cryptominers are by far the most common threat to cloud environments. Last week researchers at Intezer disclosed details about an active cryptojacking campaign targeting cloud servers with XMRig Miner. Its target cryptocurrency: Monero.
Attacker exploits known 🐳 misconfiguration ➡️ Drops undetected Golang binary ➡️ Executes XMRig Miner on Linux server
See what that looks like in Intezer Protect pic.twitter.com/KI7oDDYjPF
— Intezer (@IntezerLabs) January 13, 2021
A day later we identified a separate cryptojacking campaign, targeting Docker and Redis cloud environments. It used a malicious Docker image containing an undetected XMRig Miner.
A few weeks prior, it was an undetected Golang worm that dropped XMRig on Windows and Linux servers.
Linux is Full of Cryptominers
The Linux threat landscape is full of miners like XMRig. Linux is the dominant operating system in the cloud, making the cloud a prime target for these threats. Public cloud platforms in particular have huge processing power that attackers can use to mine cryptocurrency and generate large profits.
Attackers launching cryptominers don’t really have to use advanced tactics to compromise a server. They typically rely on a vulnerability or misconfiguration to make their way into the production environment. Once inside, they drop their payload.
The key to stopping them is not only to reduce the attack surface as much as possible, but also to monitor the runtime environment for the execution of unauthorized code—both on disk AND in-memory. Runtime protection is a second line of defense for swatting away these pesky cryptominers once the attacker gets inside.
Try the Free Intezer Protect Community Edition
Cloud Workload Protection Platforms (CWPP) like Intezer Protect are third-party tools that monitor the runtime environment to detect and terminate any unauthorized code.
A great starting point is the Intezer Protect community edition. It’s free and defends the cloud-native stack and its layers—including VMs, containers and container orchestration platforms—against the latest Linux threats.
Once a cryptominer is detected, Intezer Protect has an automatic response functionality that lets you terminate the running process on demand. After that, the platform will keep monitoring your environments to ensure you’re running 100% trusted code round-the-clock. Our new feature also identifies misconfigurations and vulnerabilities that could be exploited.

If you’re not ready to deploy, we also have a lab environment where you can simulate attacks such as backdoors, malware, and Living off the Land (LotL) threats. Contact us to access this environment.
Reducing the attack surface is an important part of any cloud security strategy. As recent cryptomining attacks have shown, our job as defenders is also to assume breach and have a protection mechanism in place to swat them away in runtime. The Linux threat landscape is also home to APTs and cybercrime groups like TrickBot, so with Intezer Protect you’ll be able to detect and respond to them too.
Protect 10 runtime assets for free.