Maze ransomware, APT41 and Lazarus highlight this month’s community samples
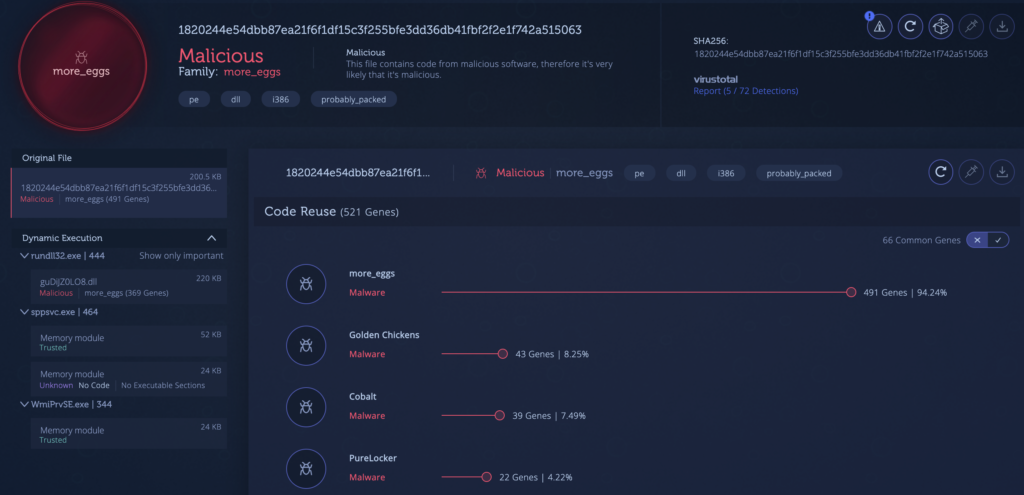
1. More_eggs variant with low Antivirus detections has modified string encoding mechanisms and other code changes
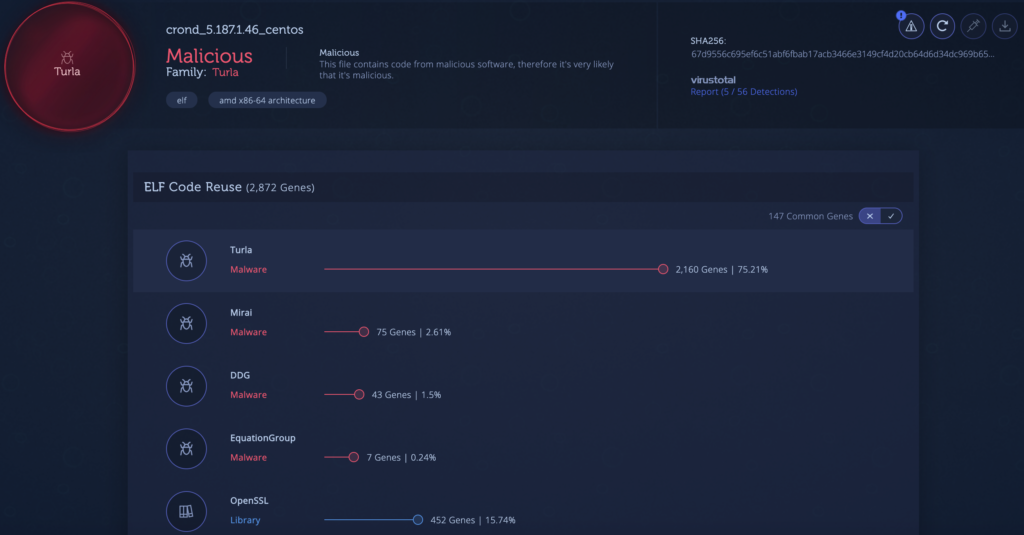
2. Penguin Turla sample shares 75 percent of its code with a sample first reported by Kaspersky in 2014
3. DragonOK (Chinese APT group) sample compiled in 2016 with no clear classification in VirusTotal shares 90 percent of its code with previously reported samples
4. Mozi malware sample first reported by CenturyLink. Like most IoT botnets this sample shares code with Mirai
5. Maze ransomware gets creative with its PDB paths “C:\Wuhan\Lab\coronashit.pdb”
6. Domestic Kitten first reported by Blackberry shares code with previous Dalvik samples from the same Iranian APT group
7. Carbanak variant unclassified on VirusTotal. Shares over 90 percent of its code with previous samples
8. Destover malware used by Lazarus group
Not an Intezer Analyze community user? Sign up for free at analyze.intezer.com to detect and classify malicious software in seconds.