1) BlackSquid [Link to Analysis]
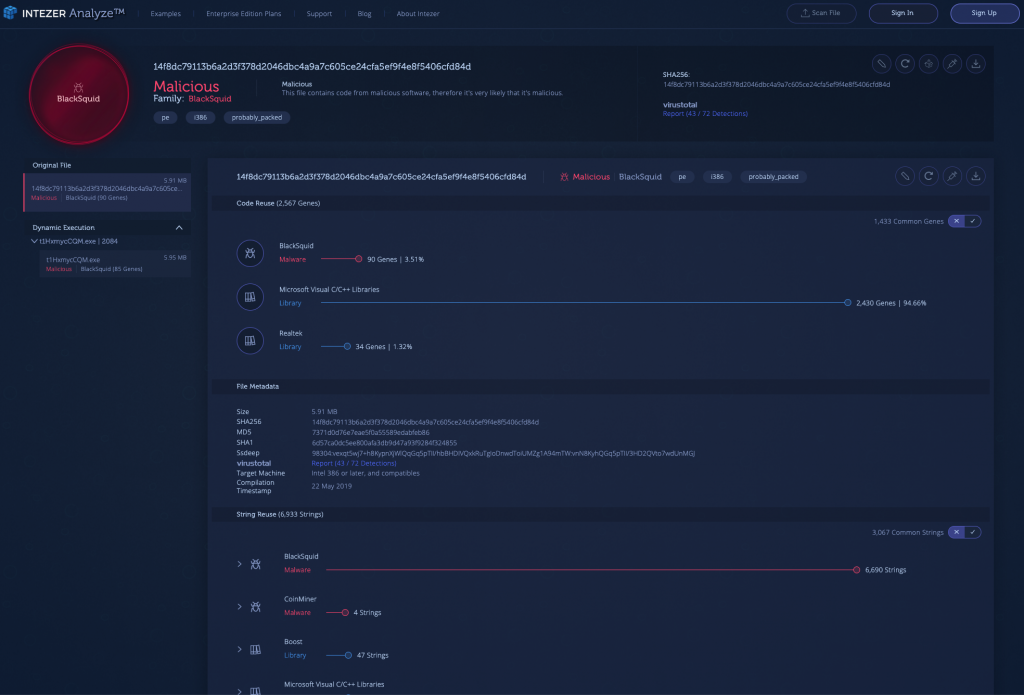
BlackSquid is a Monero crypto-miner which was recently discovered by researchers at Trend Micro. According to Trend Micro, BlackSquid uses up to eight different exploits to stealthily infect web servers and it can also laterally propagate through a network in a worm-like fashion. In order to avoid detection, the malware implements anti-virtualization, anti-debugging and anti-sandboxing methods in order to determine whether or not to deliver the miner to an infected machine. BlackSquid was observed targeting organizations primarily in Thailand and the United States during the month of June.
The sample below was uploaded to the Intezer Analyze community in early June and it is clear that only a small portion of the malware’s code is relevant. Precisely, only 2.2% of the code is classified as BlackSquid, while the remaining portions are comprised of common code and various libraries. Intezer Analyze allows its users to focus on the relevant pieces of malicious and unique code within samples, to ensure that precious time is not wasted on analyzing code from neutral libraries.
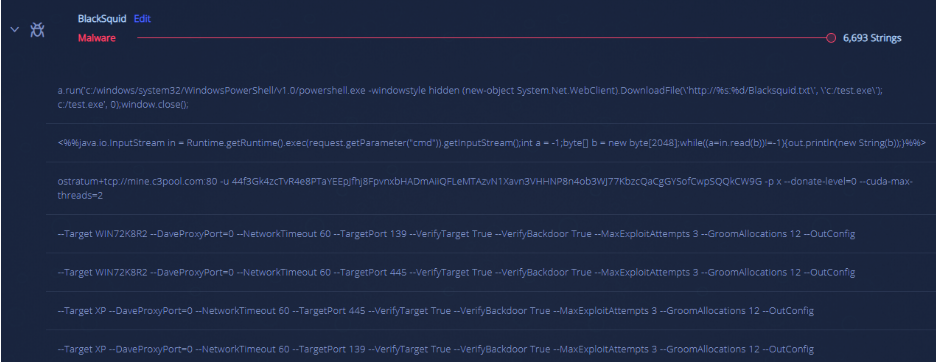
The malware’s strings also shed light into the capabilities of this crypto-miner:
2) RobbinHood Ransomware [Link to Analysis]
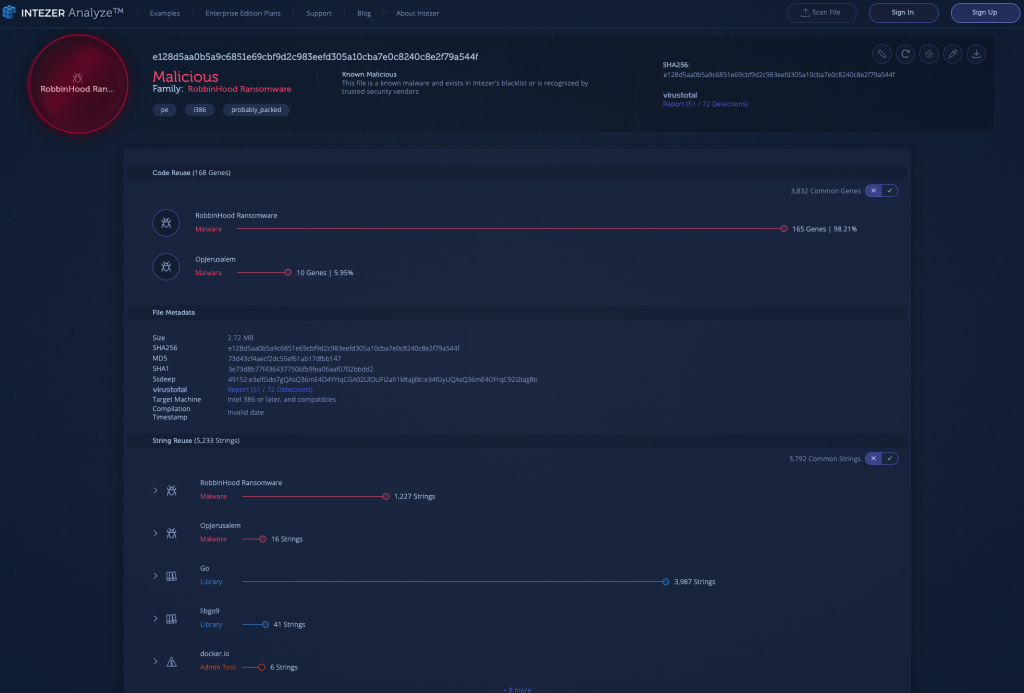
The RobbinHood ransomware attempts to incentivize its victims, for example, guaranteeing the privacy of the infected user and allowing the user to decrypt three files of his or her choosing. These features might become more common in ransomware over time, however, the primary goal of ransomware attacks remains to maximize profits for the attacker.
From a technical standpoint, RobbinHood is not drastically different from other ransomware. Once executed, RobbinHood isolates the infected machine by disconnecting all network shares and any security services. The ransomware will also remove any shadow copies and logs that it can find, and disable the Windows automatic repair mechanism. It will then encrypt the files on disk using an advanced encryption standard (AES) encryption key.
The analysis below demonstrates a clear code connection to the RobbinHood ransomware:

3) Pacifier APT [Link to Analysis]
Pacifier APT (also known as Skipper or Popeye) is widely considered to be created by the Turla Group—a Russian threat actor group which has been involved in many attacks since 2014, spanning 45 countries and targeting a wide range of industries, including education, government, pharmaceutical and research.
Pacifier APT was used in a series of attacks between 2014 and 2016 to infect victims through documents and .zip files distributed via phishing emails. The malware is considered to be an APT mainly due to its advanced evasive capabilities and the fact that it has been linked to the Turla Group. These evasion techniques include a stealthy injection process to legitimate processes running on the system in order to avoid detection.
The analysis below was uploaded to the Intezer Analyze community last month and with over 80% of shared code it shows a clear connection to Pacifier APT.
4) HiddenWasp [Link to Analysis]
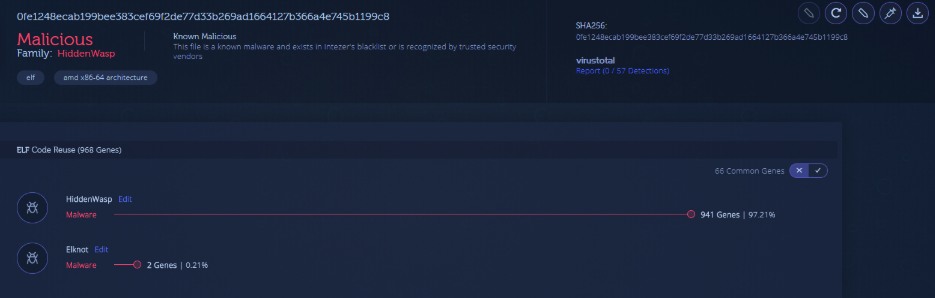
This advanced, undetected Linux malware was discovered by Intezer researchers in May. At the time the research was published, HiddenWasp had a zero-detection rate in all major anti-virus systems. Since then, some—but not all—of the engines in VirusTotal have begun to flag the malware. This is what makes identifying code similarities between malware critical for detecting sophisticated Linux threats.
HiddenWasp is used for targeted remote control, which is different from most known Linux malware which are focused on crypto-mining or DDoS activity. HiddenWasp utilizes advanced evasion techniques in order to avoid detection, which is rare to see in the Linux threat landscape, including the use of a rootkit for covert communication between different components of the malware.
The sample below uploaded by a community user shares over 95% of its code with HiddenWasp, while also containing a small amount of Elknot code, which also correlates to the findings detailed in our research. This is a prime example of an advanced malware which has taken advantage of previously leaked code and open-source projects.
5) GreedyAntd (Pacha Group) [Link to Analysis]
Pacha Group is another Linux-based threat uncovered by Intezer in February, and the malware is believed to be of Chinese origin. Pacha Group utilizes sophisticated Linux crypto-miners that exhibit remarkably aggressive behaviors, attempting to remove its “competition” from infected machines.
GreedyAntd is a crypto-miner that Pacha Group deploys to its targets once the victims have been infected, and since May, Intezer Analyze has identified new, undetected samples related to this malware family.
The analysis below shows a clear code reuse connection to GreedyAntd, while also sharing code with other crypto-miners and Mirai.