The MITRE Corporation recently released MITRE D3FEND™, a complementary framework to its industry acclaimed MITRE ATT&CK® matrix. D3FEND provides defense techniques that security teams can apply to protect their environments against cyber threats.
Intezer Analyze is a malware analysis platform. Security teams of all sizes and skill levels can quickly investigate malware, with every tool needed to do so in one place: sandboxing, static analysis, unpacking, memory analysis and genetic code sequencing. Below we explain how Intezer Analyze implements key techniques described in D3FEND.
Technique: Dynamic Analysis
Technique: Emulated File Analysis
Technique: File Content Rules
Technique: File Hashing
Technique: Byte Sequence Emulation
Technique: Memory Boundary Tracking
Technique: Service Binary Verification
Technique: Process Spawn Analysis
Technique: Script Execution Analysis
Technique: System Call Analysis
Technique: Dynamic Analysis
Definition: D3fend
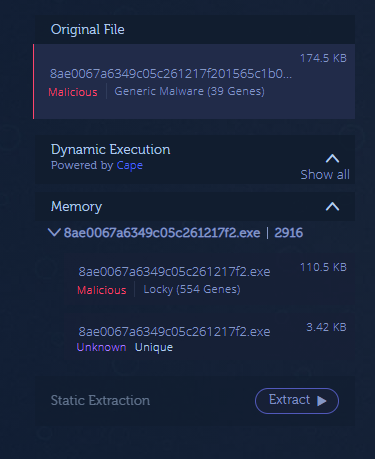
How does Intezer Analyze detect this technique? Intezer Analyze uses a dynamic execution environment based on CAPE Sandbox, where each submitted file is executed. During this process, the file’s payload is executed, including its packed and/or encrypted parts. Intezer also collects memory dumps and metadata from the process created during the execution. Finally, all of these artifacts are analyzed using a number of techniques, including genetic code sequencing, sandboxing, and static analysis, and displayed in a simple, easy to understand report.
Example: Let’s look at the analysis of this packed Locky ransomware sample. The original file is flagged as “probably_packed” and automatically sent to dynamic execution where the packed payload is extracted. The malicious payload is classified as Locky ransomware because it shares both code and capabilities with previous Locky ransomware threats. Attackers will often pack their malware in order to avoid being detected by classic Antivirus solutions, even though the payload itself is not changed.
|
File |
SHA256 |
|
Packed |
8ae0067a6349c05c261217f201565c1b05120d6fd14003a7118a95c1e9cd89de |
|
Unpacked |
690c0964936929c41e14b97dbf8a874fabe497f97d232b16007d8db10cc06128 |
Technique: Emulated File Analysis
Definition: D3fend
How does Intezer Analyze detect this technique? Intezer breaks each executable file into binary code patterns, also referred to as code ‘genes.’ These genes are referenced against Intezer’s vast database containing billions of code genes from both trusted applications and malware. Genes are also mapped to known techniques, including ATT&CK, in order to determine the origin of the binary and its behavior.
Example: The analysis of this malware reveals it belongs to the Sofacy APT group since it matches code used in previous Sofacy threats.
Technique: File Content Rules
Definition: D3fend
How does Intezer Analyze detect this technique? Intezer Analyze users can generate YARA rules for any particular malware sample. The rules are code-based, which means they will detect any variant that contains the same malicious or unique code. They are more powerful than rules based on strings or DNS information which can be easily altered by the attacker to avoid detection.
Example: Here is a YARA rule generated for Rekoobe. Visit our GitHub repository for more YARA rules.
Technique: File Hashing
Definition: D3fend
How does Intezer Analyze detect this technique? When submitting a file to Intezer Analyze, the user can either upload the file or search its hash (SHA256, SHA1 or MD5), with each analysis including the SSDeep value of the file. When a file is submitted, it is analyzed to determine if it shares code with any previously seen malware threats. If it does, the file is classified to that particular malware family or threat actor.
Example: ‘Trojan.Generic’ or threat score 41 out of 100 sound familiar? Sandboxes and EDRs (including Microsoft Defender, CrowdStrike, or SentinelOne) tend to produce generic results that lack context needed to answer necessary investigation questions. Intezer takes this malicious verdict one step further by also classifying the malware. In this analysis, the file is attributed to APT34.
Technique: Byte Sequence Emulation
Definition: D3fend
How does Intezer Analyze detect this technique? Intezer’s genetic code sequencing abilities combined with dynamic execution detect the execution of shellcode, even if it’s dropped by another file.
Example: This sample is tagged as “fileless code.” Upon further inspection, the malware is classified as Emotet because it shares over 95 percent of its code with previous Emotet samples.

Technique: Memory Boundary Tracking
Definition: D3fend
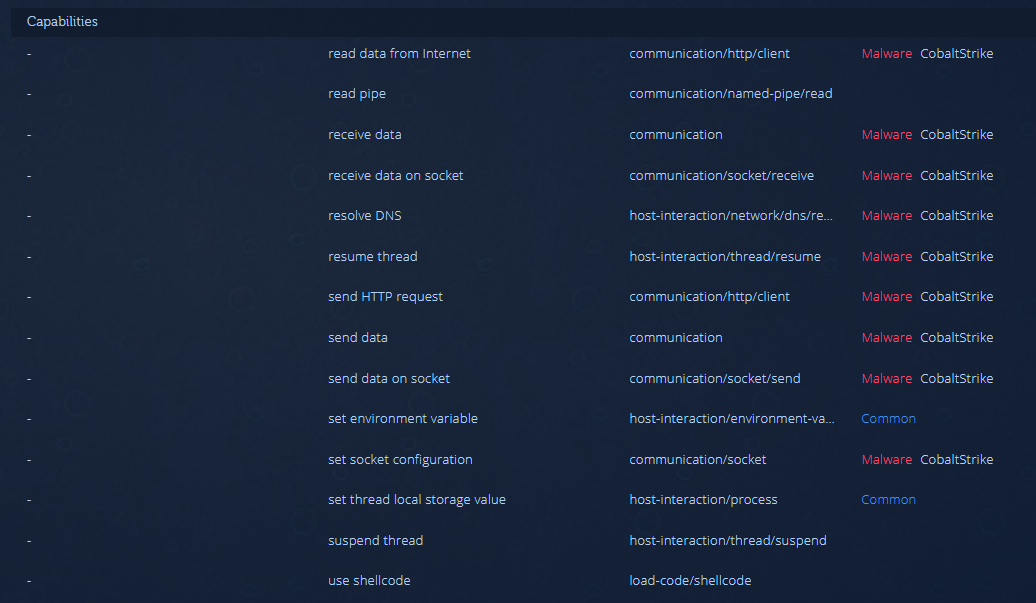
How does Intezer Analyze detect this technique? Intezer Analyze identifies executable code in any part of the process, even in trivial memory locations. As long as a file contains executable sections, Intezer extracts and analyzes the code, providing a verdict and classifying the malware based on code reuse, strings, TTPs and other indicators.
Example: In this submitted sample, the user can see the execution of code in the memory space of the process. The sample executes a Cobalt Strike payload.
Technique: Service Binary Verification
Definition: D3fend
How does Intezer Analyze detect this technique? Intezer breaks each executable file into binary code patterns, also referred to as code ‘genes.’ These genes are referenced against Intezer’s vast database containing billions of code genes from both trusted applications and malware. Genes are also mapped to known techniques, including ATT&CK, in order to determine the origin of the binary and it’s behavior.
Example: The REvil ransomware gang gained access to the infrastructure of Kaseya and deployed a malicious update to the machines managed by the service. The update contained a variant of the REvil ransomware. Upon analyzing the binary from the malicious update, the file shares code with REvil samples dating back to 2019.

Technique: Process Spawn Analysis
Definition: D3fend
How does Intezer Analyze detect this technique? Files submitted to Intezer Analyze are dynamically executed, with their output including: process name, PID, full file path and process tree.
Example: Let’s look at the analysis of a Bandook RAT sample. The original file was dynamically executed, with Intezer providing metadata about the process created during the execution. The malware injects itself into a new Internet Explorer process (iexplore.exe). In File Metadata, the user can see the full process path, hash, compilation time, PID and PPID.
Technique: Script Execution Analysis
Definition: D3fend
How does Intezer Analyze detect this technique? Intezer Analyze supports all major non-executable file types including scripts, which can be submitted as an actual script file or embedded in a Microsoft Office document or PDF file. Analyzing the script file, the user can quickly determine the type of threat and malware family, with full genetic and behavioral context.
Example: Let’s submit a powershell script file to Intezer Analyze. The file is a powershell executable, based on the analysis of its memory during the dynamic execution phase. The script then executes a Cobalt Strike payload.
Technique: System Call Analysis
Definition: D3fend
How does Intezer Analyze detect this technique? Intezer Analyze integrates with
CAPA, an open-source project that detects malicious capabilities in executable files. If system calls and other capabilities were already identified in the code of previously identified malware, the submitted file is classified to that respective malware family and TTPs are mapped to ATT&CK.
Example: Submitting a sample from the OceanLotus family, in the capabilities tab, the user can see the techniques the malware uses to execute itself, evade sandboxes, and gather information about the system.










