In this month’s community highlights we see a range of malware types, including banking trojans, exploit kits, and nation-state sponsored threats.
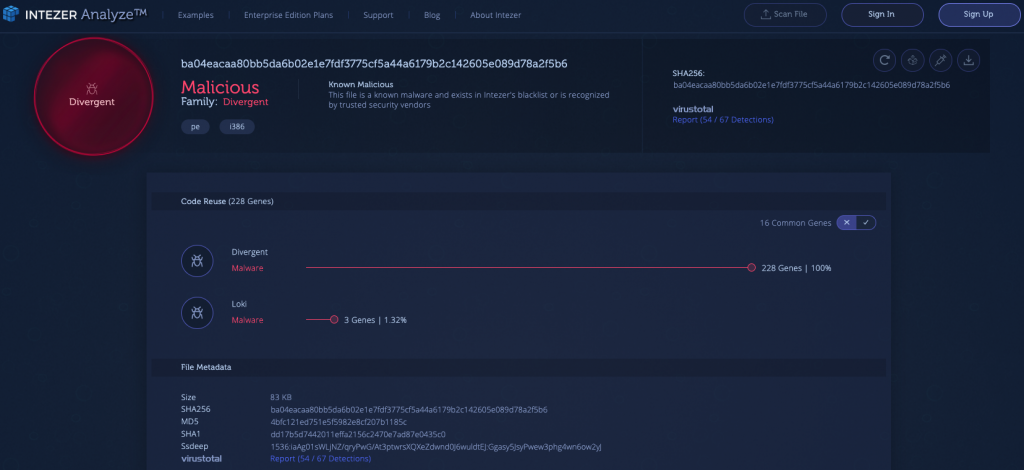
1) Divergent [Link to Analysis]
Divergent is a malware family which is used for generating profit, mainly by taking advantage of click-fraud techniques against its victims. This malware causes an infected machine to issue requests to various advertisement servers, which ultimately leads to money being funneled to the attackers.
In a recent report by Cisco Talos, divergent malware was described as using methods of fileless infection. The analysis below reveals that the initial file, which is responsible for infecting a machine and causing persistence, is able to remain active without leaving a trace on the disk. This file does, however, contain a wealth of information regarding the infection method. Just by looking at the strings, for example, you can see the full list of C2 servers which are used by this malware:
In fact, you can see two distinct lists of IP addresses here: one is used for receiving commands and exfiltrating information, while the other is used for receiving configuration updates.
Click on the analysis below to see if you can identify more relevant IOCs:
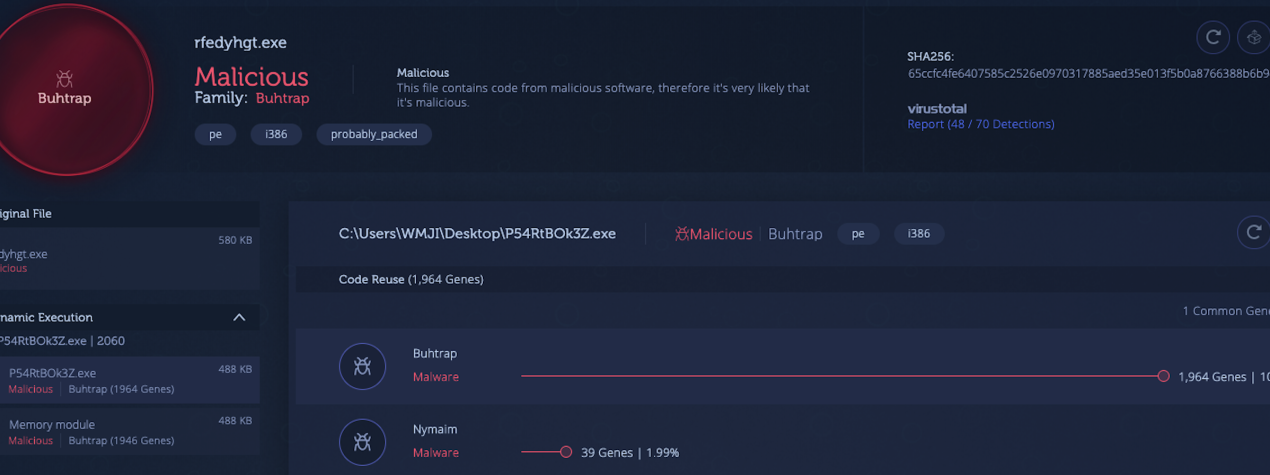
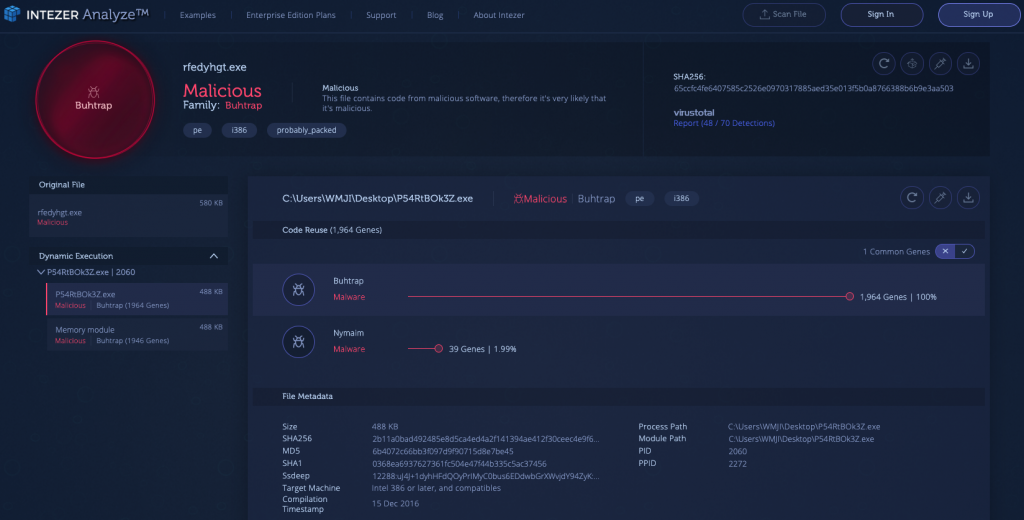
2) Buhtrap [Link to Analysis]
The Buhtrap group, with documented activity dating back to as early as 2014, initially focused its campaigns on targeting Russian businesses, particularly financial services organizations, for monetary gain. Recently, the group has pivoted its tactics to cyber espionage and is utilizing more advanced techniques. For a threat group that once primarily targeted Russian businesses, it’s interesting to see its shift towards espionage against government entities in Eastern Europe and Central Asia.
The malware used in these attacks leveraged a zero-day exploit (CVE-2019-1132) in order to elevate local privileges and obtain full access to the infected machine. The analysis below indicates a packed file with seemingly legitimate code. However, dynamic unpacking reveals it’s hiding a payload with strong code connections to Buhtrap.
3) Veil Framework [Link to Analysis]
Veil is a popular tool for bypassing common security solutions. Veil offers an open source framework to create and deploy Metasploit exploits and other malicious payloads. Using various techniques, Veil can add a layer of encryption to an existing payload, making static detection by signatures much more difficult.
In the analysis below, we can see a payload wrapped with Veil, which is written in the Go programming language. In case you missed it, Intezer Analyze now supports genetic analysis for files created in Go. Even though Veil packs the malware, genetic analysis detects its code within seconds, providing a malicious verdict and classifying the threat to the Veil family.
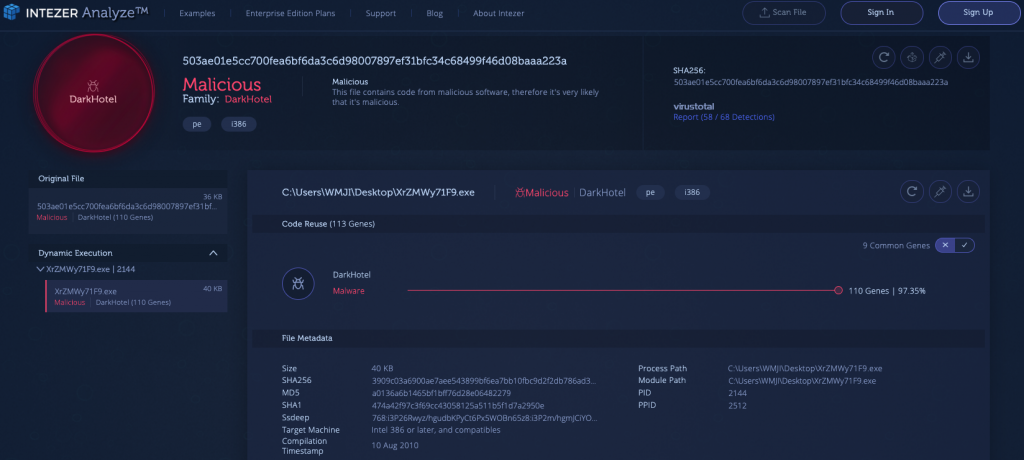
4) DarkHotel [Link to Analysis]
DarkHotel is a malware group which is notorious for targeting hotel networks globally by focusing on specific guests. The DarkHotel attacks, which were first discovered in 2014, are calculated in advance by the attacker via obtaining information about the individuals who will stay in the hotels. Once the victims log in to the insecure hotel WIFI network, they are prompted to download the initial malware payload, which is masqueraded as legitimate software updates. This initial payload will attempt to qualify the victim before downloading further malware onto their machine. When in control of the victim’s machine, DarkHotel can use a low-level keylogger to steal confidential data and also achieve persistence on the machine. DarkHotel can also spread in a botnet-like fashion and conduct DDoS attacks using its bots.
The goal behind DarkHotel appears to be credential stealing, which could hint at a possible nation-state sponsor behind this threat. Since the initial DarkHotel attacks were primarily focused in Asia targeting government officials and executives from North Korea, Japan, India, and the United States, many in the infosec community speculate that the malware’s purpose was to conduct espionage on countries possessing nuclear power.
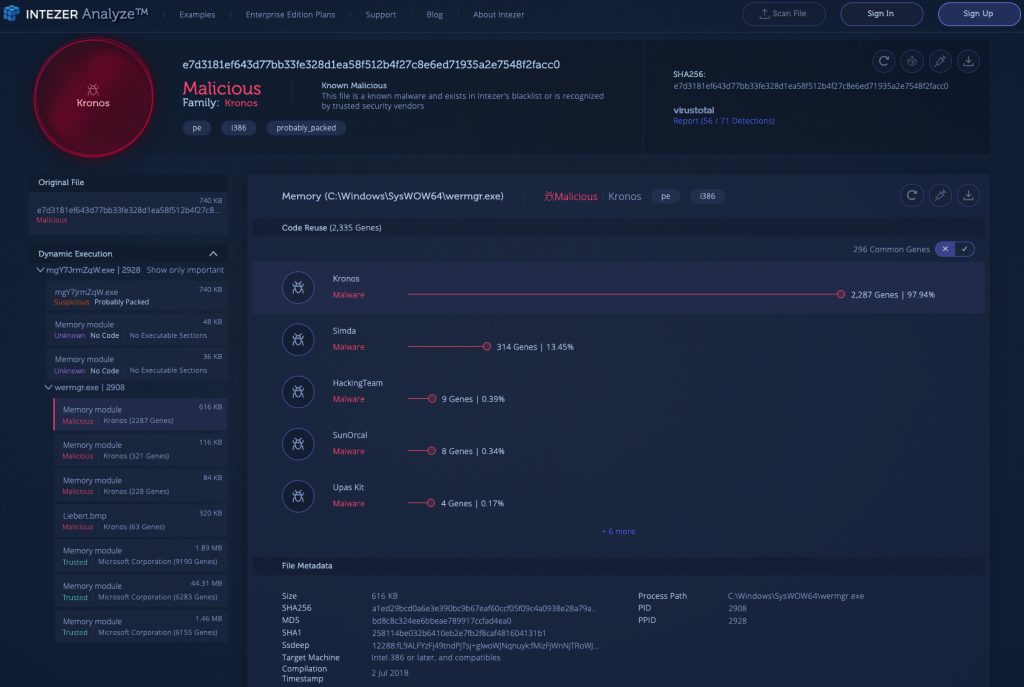
5) Kronos [Link to Analysis]
Kronos is a banking trojan which was first advertised on the black market in 2014. At the time of discovery, it was mostly spread through exploit kits such as Sundown and Rig. Once the malware infects a machine, it installs itself and achieves persistence using the common Run registry key. It then changes the browser configuration to lower the level of security on the infected endpoint. Once Kronos establishes control on a machine, its goal is to find and exfiltrate online banking credentials.
In the analysis below we can see that the sample is packed by a custom packer and four distinct payloads are injected to memory.