Software developers and malware authors share a desire to work smart, not hard
In the software development world, engineers frequently use ready-made code for various tasks, whether it involves copying a snippet from Stack Overflow, taking a library from Github, or reusing a company’s own rich, legacy code base. On the darker side of things, malware authors reusing code is a phenomenon that we see time and time again. While it makes a lot of sense to avoid reinventing the wheel, even nation-sponsored hackers search for code on Google. (This is often a surprising fact to many people in the cyber security community.)
In this blog post, we’ll present an intriguing case of code reuse in malware from publicly available code, where possibly North Korean and Iranian APT threat actors both used the same code from an example on CodeProject in crafting their malware.
As previously mentioned, malicious code reuse across different variants of the same threat actor or between different malware types is very common. This is, by the way, the base assumption that our technology is built upon. This fact was evident in both recent sophisticated threats (such as the CCleaner hack and WannaCry) and also in common generic viruses (such as BankBot). In the end, code reuse is very cost effective and can save hackers months or even years of development efforts.
In addition to reusing malicious code, malware authors also reuse legitimate, open source utility code for the same reasons every other developer uses these resources.
With Intezer’s Code Intelligence technology, we were able to witness some especially interesting cases where hackers reused code from legitimate or publicly available sources. One especially interesting case is the following:
WannaCry, Joanap and Magic Hound use code from CodeProject
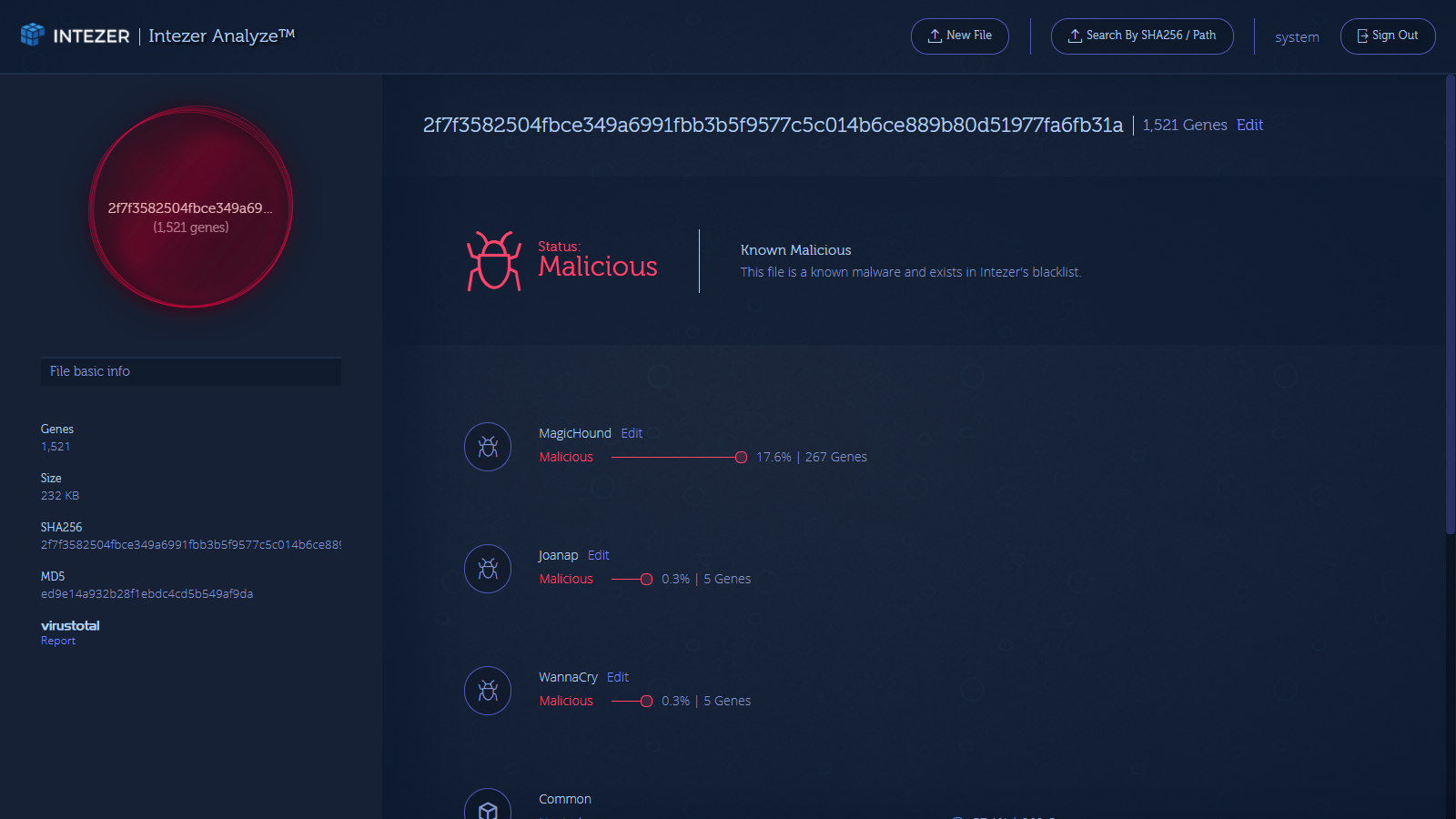
While examining a sample from the Magic Hound campaign, we discovered a strange code connection with samples from WannaCry and Joanap. These two malware families are suggested to be associated with the North Korean government:
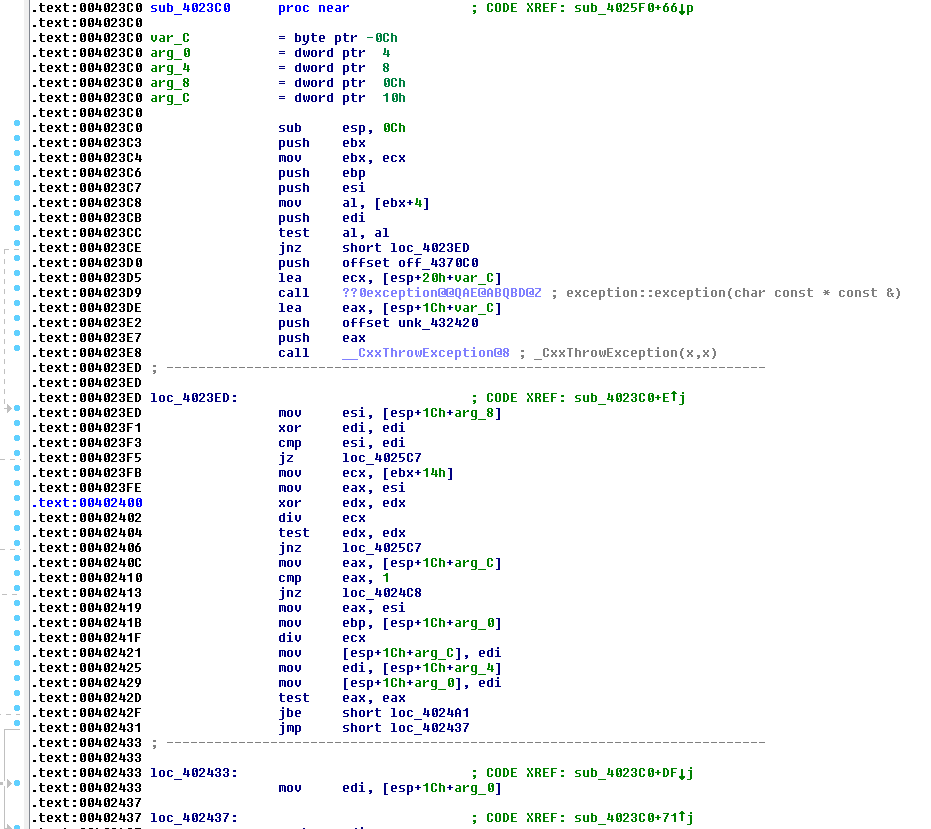
Looking deeper at the five gene connection to Joanap and WannaCry, we see that the shared code originated from the same function:
This is an AES/Rijndael encryption implementation seen in both of the malware families; interestingly enough, it was not present in any other malware families or legitimate software in our binary code database. We assumed that this code is publicly available, since a true connection between these two malware authors is very unlikely, and so we tried to trace the origins of this piece of code online. Another important fact is that this Magic Hound sample was written in C++, as you can see the code reuse of C++ libs in Intezer Analyze™:
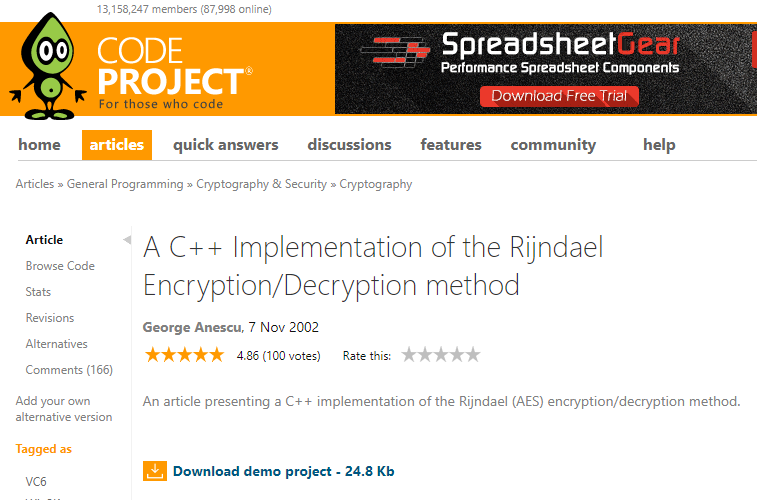
What eventually led us to the original code snippet was a simple search in Google:
“C++ Implementation AES”.
The first result was an example implementation from CodeProject. CodeProject is a very useful website for software developers to share code examples and programming tutorials. From CodeProject’s FAQ: “Code project is a community of Software development and Design developers joined together with certain common goals: to learn, to teach and to have fun programming. Developers from all over the world come together to share source code, tutorials and knowledge for free to help their fellow programmers.”
This code example dates back to 2002.
In viewing the code snippets from this CodeProject article, it was clear that this is indeed the source code used in the three malware families. Several reasons led us to this conclusion:
1. The code is almost exactly the same, except for registers and the order of a few instructions.
2. In both cases, the placement of exception handlers is exactly the same.
3. There are similar strings in the function up from the shared function.
Pulling code from publicly available online sources as part of developing malicious software may not be news to some of you, but it can occasionally appear in some surprising forms.
While code reuse isn’t uncommon, this particularly case is especially intriguing in that these two very different threat actors took the same legitimate source code directly from the internet. Probably just a coincidence, and perhaps CodeProject’s position as the first Google result helped with the odds here.
==
By exploiting the fact that malware authors constantly reuse code to your advantage, you essentially force your attackers to rewrite their entire code from scratch, which makes attacking your organization far less cost effective. In addition, identifying patterns across malware that incorporate non-threatening code can provide strong evidence toward accurately attributing future attacks.
If you have a SoC, IR, or CERT team in your organization, we invite you to check out how Intezer can help your company turn this fact into hacker’s greatest Achilles heel, and to your greatest security advantage.