In the spirit of Halloween we’re spotlighting three “spooky” threats detected by the Intezer Analyze community in October. And as a special treat, we’re giving away three code-based YARA signatures, made possible by our Genetic Malware Analysis technology, which can be used to hunt for additional variants of these threats!
1) Trickbot [Link to Analysis]
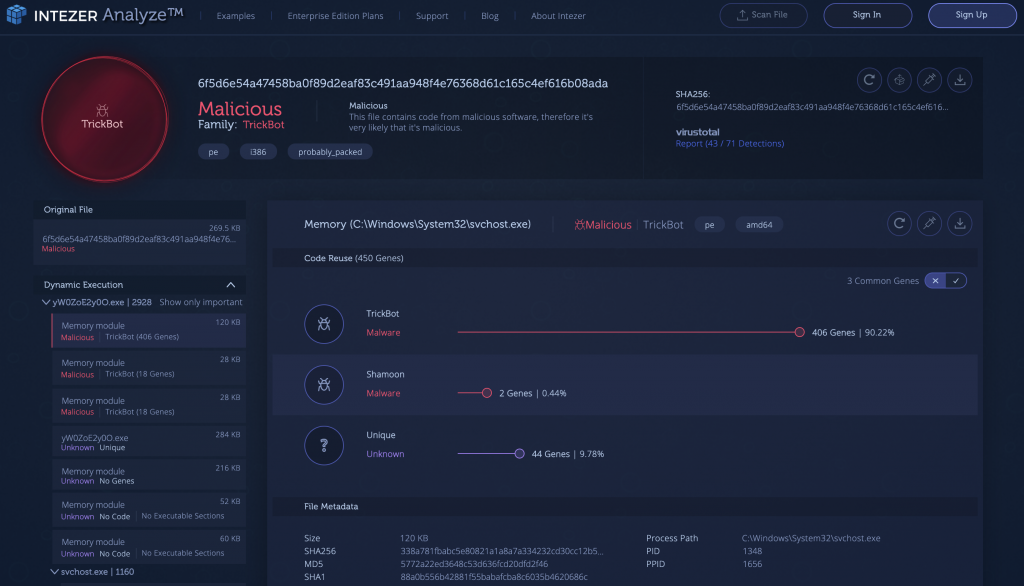
Trickbot is a common banking trojan which steals personal financial information, browser credentials, and other user data. The malware has been active since September 2016 and is believed by many to be the successor of Dyre—a similar banking trojan which infected major United States banks in 2014. Trickbot is typically dropped following a spear phishing attack via a document attachment. Once the attachment is opened, the malware infects the machine and establishes persistence. As part of this process, the threat also neutralizes security mechanisms like Windows Defender.
In the Intezer Analyze analysis below we can see precisely how Trickbot unpacks and injects itself into a legitimate svchost.exe process. Once executed, Trickbot has over 25 capabilities in its arsenal which can be used to further the attack.
2) Gh0stRAT [Link to Analysis]
Gh0stRAT is a remote access tool which can take control of a remote machine to spy on user activity, steal information, upload tools, and more. The binary code of this RAT can be traced back to the GhostNet spying operations which were uncovered in 2009 by the independent research group, Information Warfare Monitor (IWM). These operations were likely perpetrated by the Chinese government and were found to infiltrate key locations in 103 different countries, including computer systems in embassies, government offices, and media organizations.
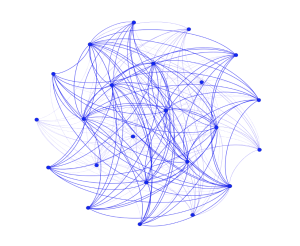
Today, the source code of Gh0stRAT is available online, which means many threat groups use it to develop their own variants. The illustration below represents several Gh0stRAT samples that were uploaded to the Intezer Analyze community in October and which share code with one another:
3) DarkComet [Link to Analysis]
DarkComet is yet another remote access trojan (RAT). It was developed by an independent programmer who advertises DarkComet as an administration tool for legitimate use. However, the developer behind this tool acknowledges that it’s also being used by attackers for malicious purposes.
DarkComet exhibits capabilities that you would typically expect from a RAT, such as taking screenshots, gaining access to a desktop user’s microphone and camera, retrieving files, controlling processes, and more. DarkComet also enables the attacker to meddle with its victims by hiding the start button and other icons, and it can even play music on the infected machine.
By leveraging Intezer Analyze’s string reuse feature, it’s very easy to understand some of the capabilities this RAT has to offer:
-
- ActiveOnlineKeylogger
- HideStartButton
For more information about DarkComet, check out the genetic analysis below.
Trickbot or Treat!
While these aforementioned threats may pose serious risks to individual end users and organizations alike, we are providing you with three vaccines (code-based YARA signatures) which can be used to detect future variants of Trickbot, Gh0stRAT, and DarkComet before they come knocking on your door. And, to make sure you’re protected year round, we encourage you to use our Genetic Malware Analysis technology to detect and classify cyber threats. You can sign up for free at analyze.intezer.com. Enjoy, and on behalf of Intezer we wish you a safe and happy Halloween!
• Trickbot: Link in GitHub
• Gh0stRAT: Link in GitHub
• DarkComet: Link in GitHub