Intro
In our last blog post we disclosed an escalation of privileges vulnerability in Microsoft Azure App Services. In this post, we’ll describe a similar vulnerability that we found in one of Microsoft’s official Azure VM extensions, known as the Azure Network Watcher Agent for Linux.
This vulnerability would allow any user of the system to escalate to root privileges, requiring only a system reboot to carry out the exploitation. We reported the vulnerability to Microsoft Security Response Center and it was soon patched and assigned CVE-2020-16995.
Azure Network Watcher VM Extension is a network performance monitoring, diagnostic, and analytics service that allows for monitoring of Azure networks. The Network Watcher Agent extension is a requirement for capturing network traffic on demand and other advanced functionalities on Azure virtual machines (VMs).
Below we will present technical details about this relatively simple but potentially deadly vulnerability.
Technical Analysis
The vulnerability we discovered is fairly straightforward. The following script is run by the Azure Network Watcher Agent on the agent’s startup, under a privileged context (root). See if you can spot the issue yourself:
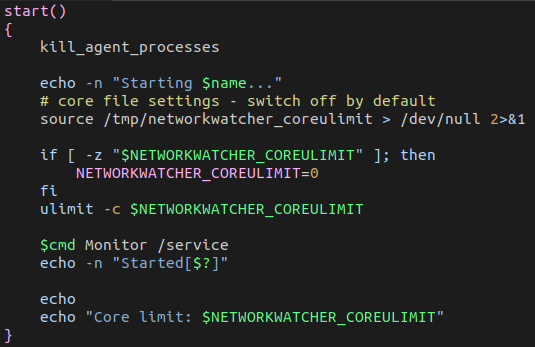
The code attempts to execute the file /tmp/networkwatcher_coreulimit. However, no such file exists on Azure VM servers. This code was probably used in the Network Watcher Agent’s development environment but forgot to be removed. This means we can create the file under an unprivileged account, supply it with our bash code, and then it will run as root, leading to an escalation of privileges.
Still, we encountered two challenges:
- The Network Watcher only runs this script after it has launched, which only happens on the system’s startup. This is a requirement for the exploit.
- The /tmp filesystem where the file resides resets on reboot. We had to find a way to create the file after the system boots but before the agent executes it, which leaves us a small window of opportunity since it happens almost immediately after the system’s startup.
To solve the second problem, we had to better understand the Network Watcher Agent.
We reviewed the Network Watcher Agent’s systemd file at /run/systemd/generator.late/Azure.service:
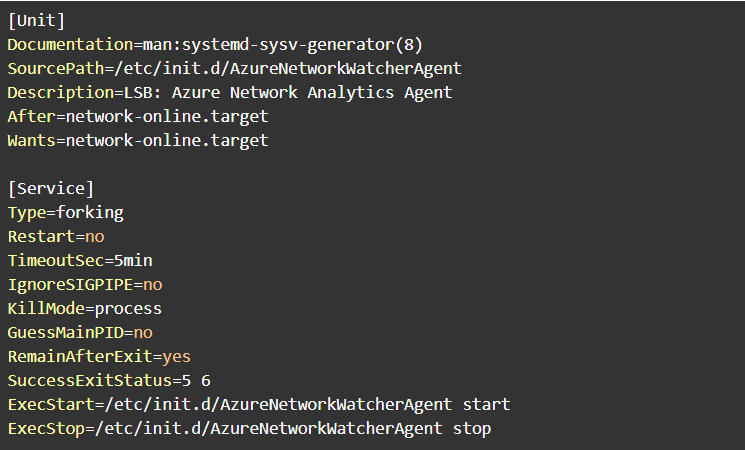
As can be seen above this service runs after the “network.target” systemd event, which happens early on and makes it nearly impossible to access the system externally in this small window of time.
Luckily, Azure Virtual Machines support a systemd feature allowing unprivileged users to create systemd services.
We created a service under the systemd user services directory “~/.config/systemd/user” and instructed it to run before network.target.
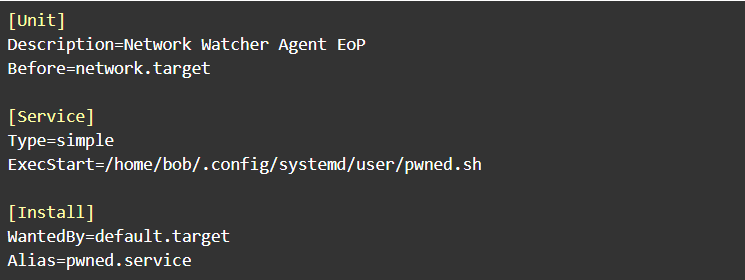
The pwned.sh script will create the vulnerable networkwatcher_coreulimit file which adds our unprivileged user bob to sudoers when executed:

After a system reboot our unprivileged user is able to escalate to root:

Conclusion
In this post we detailed a simple escalation of privileges vulnerability identified in the Network Watcher Agent, a first party Azure VM extension. We immediately reported this vulnerability to Microsoft Security Research Center and it is now fixed.
In situations where vulnerabilities are out of the control of the cloud consumer, monitoring the runtime environment to detect post vulnerability exploitation and other in-memory threats is an important last line of defense.
Use the Intezer Protect Community Beta to protect up to 10 cloud servers and containers against unauthorized code. Try it Free






