Introduction
Linux desktop remains an unpopular choice among mainstream desktop users, making up a little more than 2% of the desktop operating system market share. This is in contrast to the web server market share, which consists of 70% of Linux-based operating systems. Consequently, the Linux malware ecosystem is plagued by financial driven crypto-miners and DDoS botnet tools which mostly target vulnerable servers.
This explains our surprise when in the beginning of July, we discovered a new, fully undetected Linux backdoor implant, containing rarely seen functionalities with regards to Linux malware, targeting desktop users.
Throughout our investigation, we have found evidence that shows operational similarities between this implant and Gamaredon Group. We have investigated this connection and in this blog we will present a technical analysis of the tool.
We have named the implant EvilGnome, for its disguise as a Gnome extension. The malware is currently fully undetected across all major security solutions:

Figure 1: VirusTotal detections of an EvilGnome sample
We believe this is a test version that was uploaded to VirusTotal, perhaps by mistake. The implant contains an unfinished keylogger functionality, comments, symbol names and compilation metadata which typically do not appear in production versions. EvilGnome’s functionalities include desktop screenshots, file stealing, allowing capturing audio recording from the user’s microphone and the ability to download and execute further modules.
Gamaredon Group Connection
Gamaredon Group is an alleged Russian threat group. It has been active since at least 2013, and has targeted individuals likely involved with the Ukrainian government. Gamaredon Group infects victims using malicious attachments, delivered via spear phishing techniques. The group’s implants are characterized by the employment of information stealing tools—among them being screenshot and document stealers delivered via a SFX, and made to achieve persistence through a scheduled task. Gamaredon Group primarily makes use of Russian hosting providers in order to distribute its malware.
Our investigation into EvilGnome yielded several similarities between the threat actors behind EvilGnome and Gamaredon Group:
Hosting Similarities
The operators of EvilGnome use a hosting provider that has been used by Gamaredon Group for years, and continues to be used by the group.
More specifically, EvilGnome’s C2 IP address (195.62.52.101) was resolved two months ago by the domains gamework.ddns.net and workan.ddns.net, associated with the Gamaredon Group:

Figure 2: RiskIQ EvilGnome C2 IP query
We used RiskIQ to map the history of the gamework.ddns.net domain:

Figure 3: gamework.ddns.net DNS timeline
The finding shows that EvilGnome operates on an IP address that was controlled by the Gamaredon group two months ago.
Infrastructure Similarities
While investigating the EvilGnome C2, we observed that it served SSH over port 3436.
We then checked for the 3436 port over three currently operating Gamaredon Group C2 servers, and found one server with this port open, serving SSH:
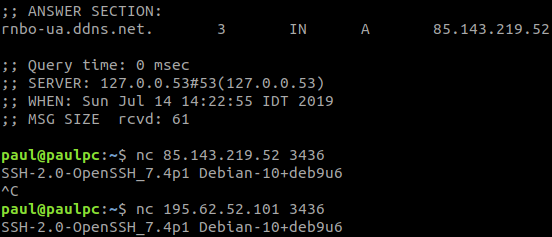
Figure 4: SSH served on port 3436 both on EvilGnome C2 and Gamaredon’s rnbo-ua.ddns.net
We proceeded to scan for this network fingerprint under EvilGnome’s host provider and we identified two additional servers with domain names similar to the naming pattern of Gamaredon domains (the use of the .space TTLD and ddns):
- 185.158.115.44 -> kotl.space
- 185.158.115.154 -> clsass.ddns.net
Tool Similarities
Gamaredon Group does not use any known Linux implants. It is difficult to make comparisons between tools built for different operating systems because they are developed with different challenges and objectives in mind. We can, however, observe similarities at a high-level. The techniques and modules employed by EvilGnome—that is the use of SFX, persistence with task scheduler and the deployment of information stealing tools—remind us of Gamaredon Group’s Windows tools. We present a thorough analysis of EvilGnome in the following section.
Technical Analysis
Deployment with Makeself SFX
This implant is delivered in the form of a self-extracting archive shell script created with makeself:
- “makeself.sh is a small shell script that generates a self-extractable compressed tar archive from a directory. The resulting file appears as a shell script (many of those have a .run suffix), and can be launched as is. The archive will then uncompress itself to a temporary directory and an optional arbitrary command will be executed (for example an installation script). This is pretty similar to archives generated with WinZip Self-Extractor in the Windows world.”
Interestingly, the tool’s operator did not omit metadata from the generated makeself SFX. The packaging date, development paths and the tool’s filename were all left exposed. We can observe that the sample is very recent, created on Thursday, July 4:


Figure 5: Makeself packaging metadata and the archived files’ metadata
As can be observed in the illustration above, the makeself script is instructed to run ./setup.sh after unpacking.
Using makeself’s options, we are able to instruct the script to unpack itself without executing:

Figure 6: Unpacking Makeself
The archive contains four files:
- gnome-shell-ext – the spy agent executable
- gnome-shell-ext.sh – checks if gnome-shell-ext is already running and if not, executes it
- rtp.dat – configuration file for gnome-shell-ext
- setup.sh – the setup script that is run by makeself after unpacking
The setup script installs the agent to ~/.cache/gnome-software/gnome-shell-extensions/, in an attempt to masquerade itself as a Gnome shell extension. Gnome shell extensions allow tweaking the Gnome desktop and add functionalities. They are the desktop equivalent to browser extensions.
Persistence is achieved by registering gnome-shell-ext.sh to run every minute in crontab.
Finally, the script executes gnome-shell-ext.sh, which in turn launches the main executable gnome-shell-ext:

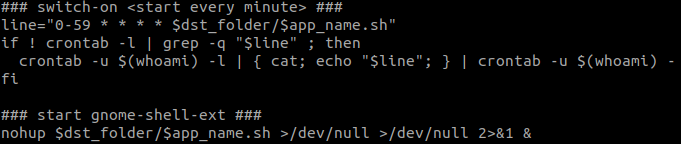
Figure 7: setup.sh
The Spy Agent
Analyzing the agent with Intezer Analyze demonstrated to us that the code was never seen before by the system:
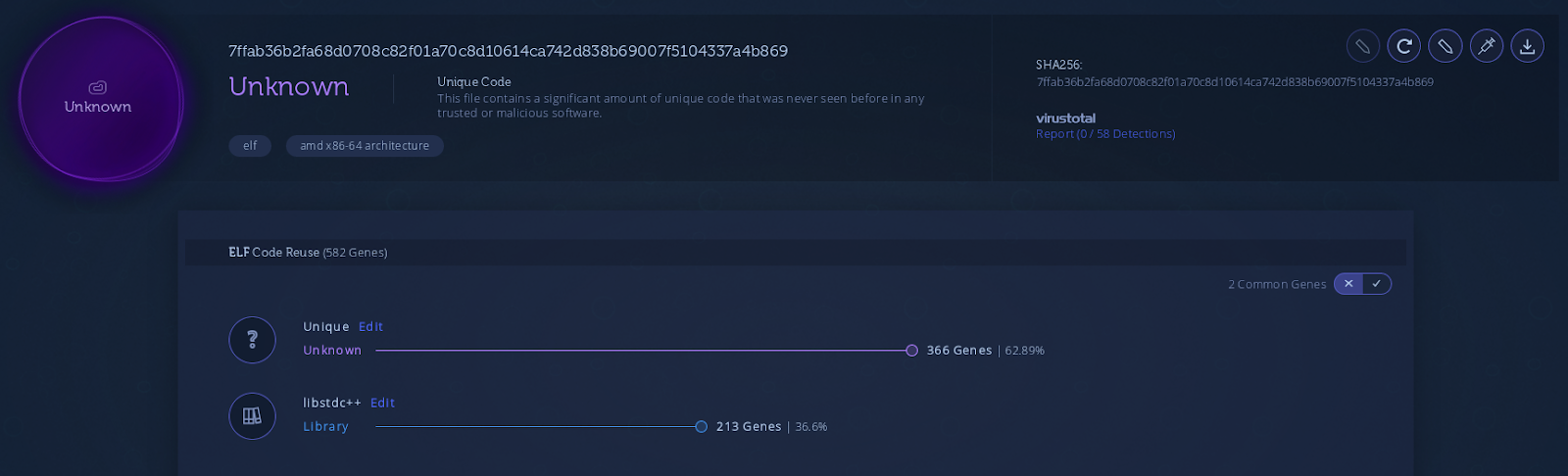
Figure 8: Intezer Analyze report of the Spy Agent sample
This large amount of unique genes located within this file is not a trend we regularly see in Linux files and therefore it seems suspicious.
The Spy Agent was built in C++, using classes with an object oriented structure. The binary was not stripped, which allowed us to read symbols and understand the developer’s intentions.
At launch, the agent forks to run in a new process. The agent then reads the rtp.dat configuration file and loads it directly into memory:

Figure 9: Loading configuration from rtp.dat
We marked interesting fields within the configuration file:

Figure 10: Configuration dissection
The first four bytes are a hexadecimal representation of the C2’s IP address:
0x65343ec3 -> 0xc3.0x3e.0x34.0x65 -> 195.62.52.101
Modules
The spy agent contains five modules called “Shooters”:

Figure 11: “Shooter” modules
ShooterSound – captures audio from the user’s microphone and uploads to C2
ShooterImage – captures screenshots and uploads to C2
ShooterFile – scans the file system for newly created files and uploads them to C2
ShooterPing – receives new commands from C2
ShooterKey – unimplemented and unused, most likely an unfinished keylogging module
Each module is run in a separate thread, and access to shared resources (such as the configuration) is safeguarded by mutexes.
The modules encrypt their output and decrypt data from the C2 with RC5 with the key “sdg62_AS.sa$die3”, using a modified version of a Russian open source library https://webhamster.ru/site/page/index/articles/projectcode/157:

Figure 12: RC5 library
On connection failure, or if instructed by the C2, these modules store their output at ~/.cache/gnome-software/gnome-shell-extensions/tmp/:
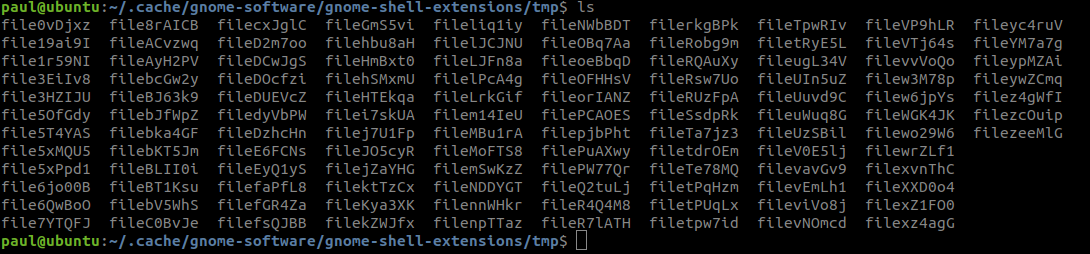
Figure 13: Stored files
We will now dive into each of the five modules and their options:
ShooterPing
The ShooterPing module processes commands received from the C2:

Figure 14: C2 commands
These include:
- Download & execute new files
- Set new filters for file scanning
- Download & set new runtime configuration
- Exfiltrate stored output to C2
- Stop the shooter modules from running
The other modules run at a constant interval between each run, as defined by one of the configuration parameters. The C2 is able to control this interval via downloading new parameters through ShooterPing.
ShooterFile
The ShooterFile module uses a filter list to scan the filesystem, while ignoring specific files and folders as shown in the following illustration:

Figure 15: File scanning filter
We can see from the filter_accepted_files list that the agent’s purpose is to steal document related files. However, the list is not used by the malware and further indicates that this is a work in progress.
ShooterAudio

Figure 16: Capturing audio with PulseAudio
The ShooterAudio module uses PulseAudio to capture audio from the user’s microphone.
Using default configuration from rtp.dat, the module records only a size of 80,000 bytes of audio per iteration. Consequently, the module only records audio for a brief moment, making this module non-functional until a larger recording size is set by the C2.
ShooterImage
This module opens a connection to the XOrg Display Server, which is the backend to the Gnome desktop. It uses the Cairo open source library to take screenshots of the user’s desktop.
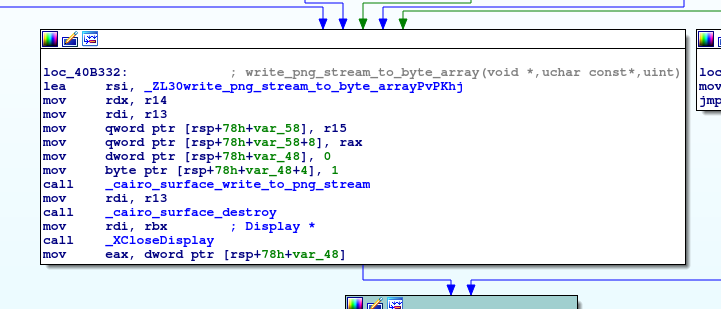
Figure 17: Screenshot capturing using XOrg Server
Prevention and Response
We recommend to Linux users who want to check whether they are infected to check the “~/.cache/gnome-software/gnome-shell-extensions” directory for the “gnome-shell-ext” executable. We have also created a custom YARA rule, based on code reuse technology, for detecting future variants of EvilGnome.
Conclusion
EvilGnome is a rare type of malware due to its appetite for Linux desktop users. Throughout this post, we have presented detailed infrastructure-related evidence to connect EvilGnome to the actors behind the Gamaredon Group. We believe this is a premature test version. We anticipate newer versions to be discovered and reviewed in the future, which could potentially shed more light into the group’s operations.
Genetic Analysis
The EvilGnome malware variant is now indexed in Intezer’s genetic database. If you have a suspicious file that you suspect to be EvilGnome, you can upload it to Intezer Analyze in order to detect code reuse to this threat family and many others. You are welcome to try it for free in our community edition.

Figure 18: Intezer Analyze report of the Spy Agent sample
IOCs
EvilGnome:
a21acbe7ee77c721f1adc76e7a7799c936e74348d32b4c38f3bf6357ed7e8032
82b69954410c83315dfe769eed4b6cfc7d11f0f62e26ff546542e35dcd7106b7
7ffab36b2fa68d0708c82f01a70c8d10614ca742d838b69007f5104337a4b869
195.62.52[.]101
Gamaredon Group:
185.158.115[.]44
185.158.115[.]154
clsass.ddns[.]net
kotl[.]space







